Keys to the kingdom: Mitigate organisational risk through PAM
Learn how to strengthen your enterprise security through internal employee privileged access
May 18, 2021 | By Kory Patrick, Scott McCallum and David Sickel

In the world of identity, privileged access management (PAM) is considered a must-have. Akin to holding the keys to your network security kingdom, a successful PAM program controls and monitors your internal employee privileged user activity and access. Think: addressing and mitigating vulnerabilities that are presented when users are given high-level permissions and require access to critical systems.
A subset of identity access management (IAM), PAM does more than just ensure the right user has the right access at the right time—PAM layers on additional control and auditing over privileged users and activities. Essentially, if you’re doing anything to mitigate risk in the identity space, make sure you start with PAM.
Why provide privilege in the first place?
Privileges are important and necessary for business operations—providing users, applications and other system processes the appropriate rights to access resources and information to complete mission-critical tasks and keep business as usual. The problem? It’s a security risk. Threat actors are working to penetrate your organisation’s perimeter to hack those privileged accounts—accessing unauthorised, sensitive and confidential information.
To put it lightly, PAM is critical to protect the business from threats
The lack of visibility and awareness of privileged users, accounts and credentials makes it difficult for organisations to detect malicious use of these—harmful activities can go on for an extended period without recognition. These accounts can add up and become long forgotten, providing dangerous backdoor access for attackers. While most organisations consider a “hacker” to be an external threat, in many instances it could be an inside job. Former or current employees that may have uncontrolled access to privileged accounts may also be a threat—benefitting from the internal knowledge of where protected assets and information are and how to get to them.
Benefits of having a PAM programme in place
Besides the obvious benefit of securing your organisation’s assets that much more, there are some additional advantages for implementing a PAM programme. From an executive point of view, PAM programmes provide an extra layer of security to keep your organisation safe from a mega breach—and away from negative publicity. Being in the crosshairs of bad press can affect potential customers, confidence and loyalty.
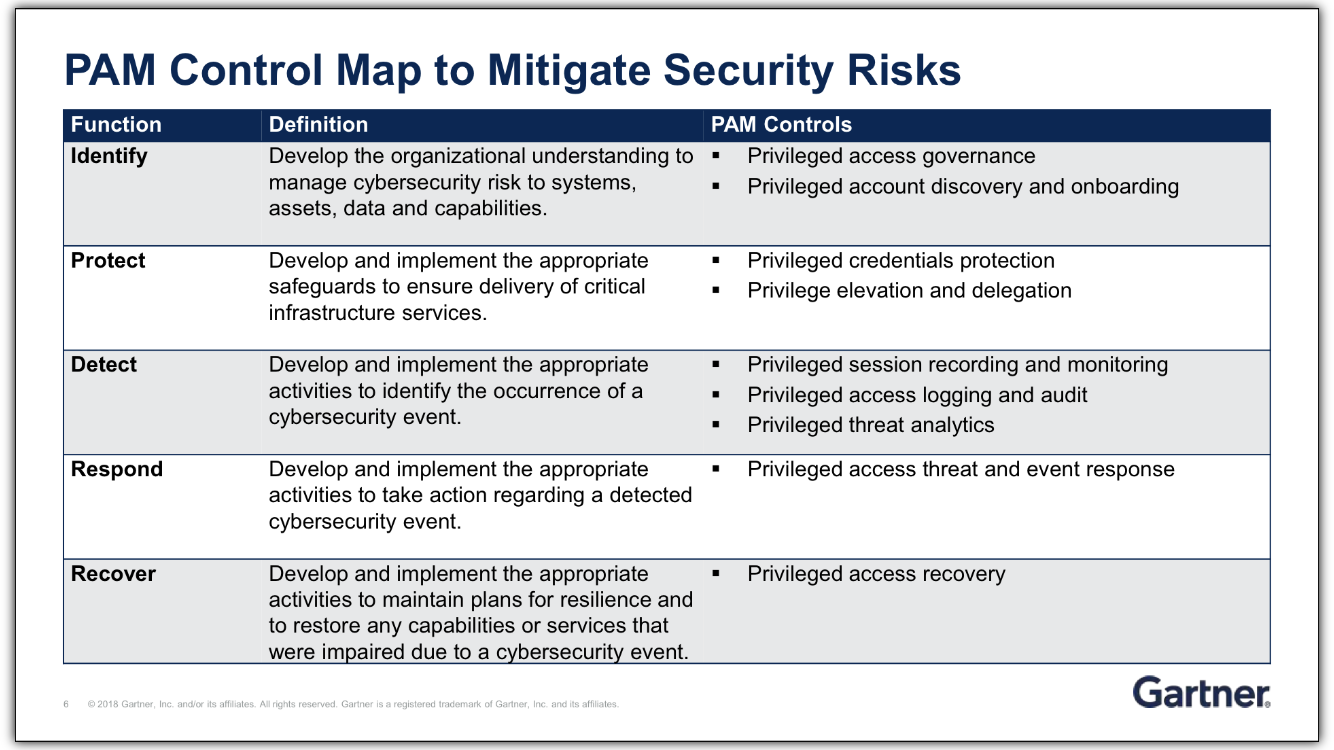
PAM Control Map
According to Gartner, “Security and risk management technical professionals must architect privileged access control capabilities to avoid exploitation scenarios and resist advanced persistent attacks.” The following is Gartner’s suggested process for implementing PAM and mitigating security risks:
You’ve got big plans— protect them
Ultimately, protecting your business requires more than just crossing your fingers. It means thinking differently to safeguard your most valuable assets.
Our risk and security specialists help identify talent who can redefine security processes to improve your capabilities and strengthen your security posture.
Kory Patrick is a risk and security solution executive at TEKsystems. He develops full-stack advisory and consulting solutions for the enterprise environment focused on reducing risk to the business by addressing security, privacy and compliance challenges.
Scott McCallum is a solutions architect and the IAM product line lead at TEKsystems. He is a seasoned IT security professional with an extensive background in enterprise identity and access management solutions and privileged account risk mitigation, with a focus on customer-facing roles.
David Sickel is a practice architect for the IAM product line at TEKsystems. He is a seasoned IT security professional with extensive background in background in enterprise identity and access management solutions and privileged access management solutions with, a focus on technical implementation roles.